Browser Based Ad Blocking
2022-11-27
TD;DR⚓
ads suck, but also suck for security reasons⚓
*sigh* Fucking ads.
Ok, maybe not the best example; pop ups are dead, and IE is mostly dead, but still.
...XP will out live us all.
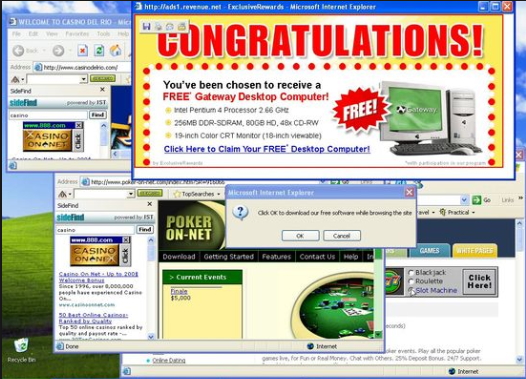
Main thing is malvertising, do a search in Google and/or Bing with a vanilla browser for something like "download putty" and see what you get. Follow the most prominent links, pretty soon you'll have a dodgy site and some malware downloading. There are other types as well.
https://en.wikipedia.org/wiki/Malvertising
https://www.crowdstrike.com/cybersecurity-101/malware/malvertising/
Also confidentiality / privacy side of it. They gunk up logging with mostly noise. They chew up more bandwidth than you'd think, but mostly it's hogging system resources and optimisations favouring the ad networks that result in slow rendering times and just general sluggishness. Pick a site, open DevTools, see where all those resources are spent, probably >50% is ads.
There's also these kinds of things, from those types of organisations.
Anyway, all this should make getting a change approved to get rid of ads pretty easy; approximately zero push back from anyone, except maybe marketing, but they don't need know.
https://www.cyber.gov.au/acsc/view-all-content/publications/essential-eight-maturity-model
https://www.cyber.gov.au/acsc/view-all-content/advice/guidelines-system-hardening
Essential 8 maturity levels 1, 2, 3
ISM 1485
"Web browsers do not process web advertisements from the internet"
https://media.defense.gov/2019/Jul/16/2002158057/-1/-1/0/CSI-BLOCKING-UNNECESSARY-ADVERTISING-WEB-CONTENT.PDF
"BLOCKING UNNECESSARY ADVERTISING WEB CONTENT"
https://www.stigviewer.com/stig/mozilla_firefox/2021-06-09/finding/V-223174
https://www.stigviewer.com/stig/mozilla_firefox/2021-12-01/finding/V-251569
Finding ID V-223174 -- "Enhanced Tracking Protection must be enabled."
Finding ID V-251569 -- "Firefox Enhanced Tracking Protection must be enabled."
https://www.stigviewer.com/stig/microsoft_edge/2021-02-16/finding/V-235766
V-235766 -- "Tracking of browsing activity must be disabled"
how to block those sucky ads?⚓
Two main ways to do it; network and application layers.
But which is better?
Block at the network, great nice and broad catch all solution.
Works for those devices where you don't have much access to the host (BYOD, "smart" somethings, IOT, etc). But can also results in page rendering issues, (artefacts like those white empty frames of nothing that just look broken). And what happens when hosts (laptop) go off the corp network?
Increasingly the ad networks are checkcing if their ad loads and nag / throw a tantrum if not detected.
Block in the browser, integrates with the DOM, almost no rendering issues. Usually blocks the ad nework's ad check thing. That's a cat and mouse game you'll mostly win, but not 100%.
...or
 ...that "defense in depth" thing people keep talking about.
...that "defense in depth" thing people keep talking about.
Firefox and Edge make it nice and easy with native functionality, just need to enable it. Chrome, not so easy, leave that for you to ponder why that might be.
As of time of writing, have to use a third party extension for Chrome (something like uBlock Origin, native options for Firefox and Edge will block most of it, but uBlock Origin blocks more and does it better.
I'll be doing things with GPOs (well LGPO really) here, makes it easy for everyone (anyone?) reading along. If you have better tooling like Intune, trust you to do the needful.
Initial testing / stuffing about getting familiar with it, Windows Sandbox great for that. If you've not used it before, check it out, too few seem to know it exists, and end up doing things the hard way for no reason. It's kind of like PowerShell, in the sense that you'll rather quickly find it super handy, and wonder how the hell you ever got anything done without it before.
https://techcommunity.microsoft.com/t5/windows-kernel-internals-blog/windows-sandbox/ba-p/301849
https://learn.microsoft.com/en-us/windows/security/threat-protection/windows-sandbox/windows-sandbox-overview
...or, the Leeroy Jenkins method works to.
Network layer, out of scope for this post. Might write another one. Check these out though.
https://live.paloaltonetworks.com/t5/blogs/new-dns-security-category-adtracking/ba-p/499482
https://docs.pi-hole.net/
https://help.amplifi.com/hc/en-us/articles/360018569574-Advanced-Settings-in-the-Web-UI
https://help.ui.com/hc/en-us/articles/9794438523799-UniFi-Network-Ad-Blocking
https://openwrt.org/docs/guide-user/services/start
Firefox⚓
Mozilla call it "tracking protection".
https://support.mozilla.org/en-US/kb/enhanced-tracking-protection-firefox-desktop
Can configure it with the policy templates here.
https://github.com/mozilla/policy-templates
Couple of ways to go about it, mostly centered around the browser.contentblocking.category setting.
- Method 1 / "custom" - with all the things enabled
- Method 2 / "strict" - also enables all the sittings
The might be a difference, but I can't find it. If a little bit of JSON is ok with you, go with method 2.
method 1 ("custom")⚓
GPO
User or Computer
Administrative Templates > Mozilla > Firefox > Tracking Protection
https://github.com/mozilla/policy-templates#enabletrackingprotection
Enable those:
- Enabled
- Fingerprinting
- Cryptomining
- Do not allow tracking protection preferences to be changed
![]()
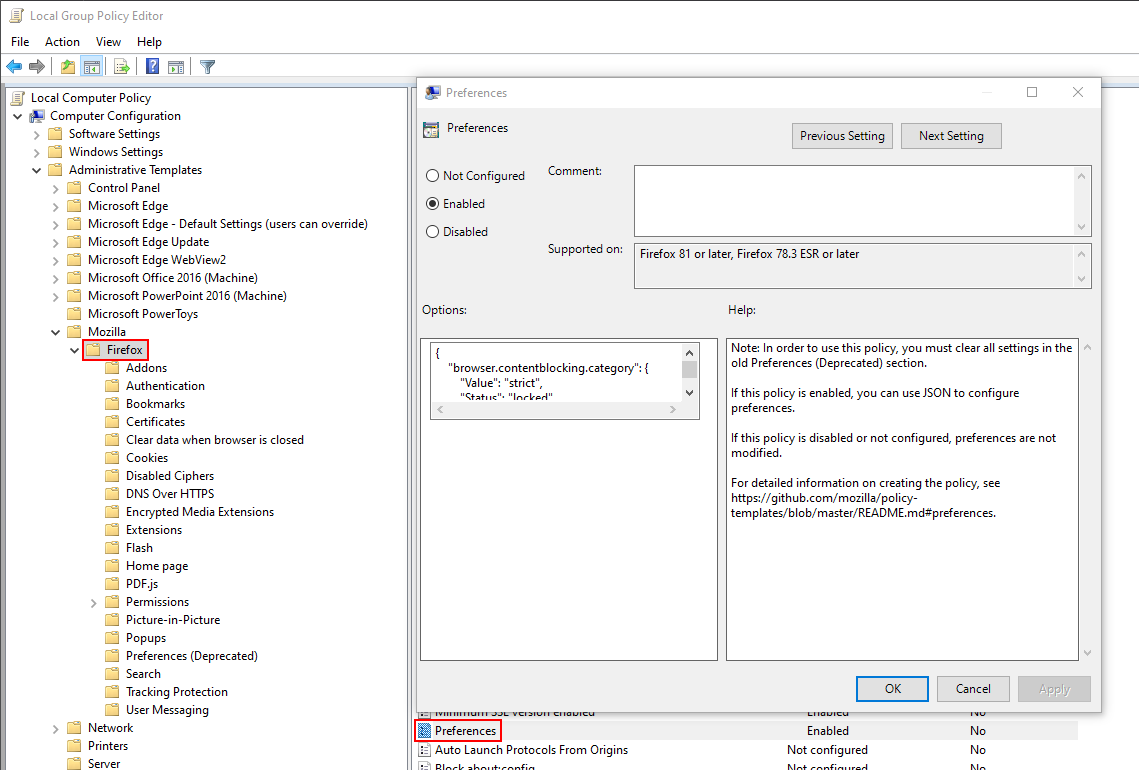
method 2 ("strict")⚓
GPO
User or Computer
Administrative Templates > Mozilla > Firefox > Preferences
Define some settings in JSON, copy paste.
https://github.com/mozilla/policy-templates/blob/master/README.md#preferences
{
"browser.contentblocking.category": {
"Value": "strict",
"Status": "locked"
}
}
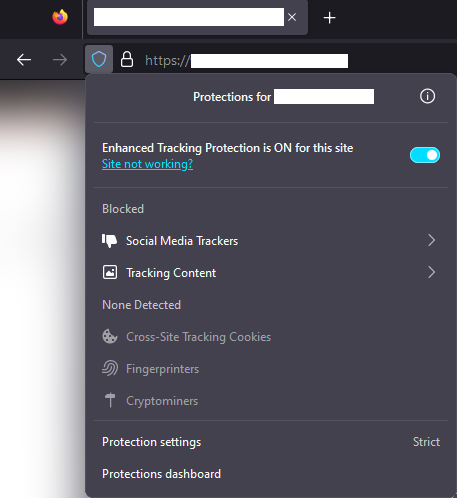
test⚓
Find a web page with a bunch of ads, should now see less than normal. There should also be a shield icon near the address bar you can click on.
Edge⚓
Microsoft call in "tracking prevention".
https://learn.microsoft.com/en-us/microsoft-edge/web-platform/tracking-prevention
Can configure it with the policy templates here.
https://www.microsoft.com/en-us/edge/business/download
GPO
User or Computer
Administrative Templates > Microsoft Edge > Block tracking of user's web-browsing activity
Enable that
![]()
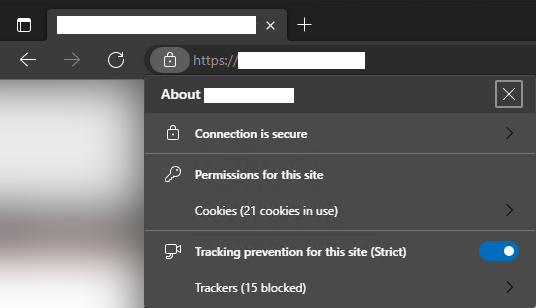
test⚓
Find a web page with a bunch of ads, should now see less than normal. There should also be a pad lock icon near the address bar you can click on.
bonus points: checkout "Super Duper Secure Mode"⚓
While you're already poking about Edge, suggest having a read, and consider enabling "Super Duper Secure Mode". At time of writing it's not in any baseline that I know of, but it's probably coming.
// TODO: write that browser hardening thing you've been meaning to
https://microsoftedge.github.io/edgevr/posts/Super-Duper-Secure-Mode/
https://learn.microsoft.com/en-us/deployedge/microsoft-edge-security-browse-safer
https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#enhancesecuritymode
Chrome⚓
No native functionality to block ads, in the browser made by a company that makes most of it's money selling ads on the internet, that has majority market share of browsers...

slight rant / considerations for YOU to make⚓
Personally, think Chrome should be avoided, in both home and enterprise. Core browser is great (Chromium), it's all the Google stuff on top that's not great. But if you're stuck with it, need to make the best of it. To do that, recommend uBlock Origin (uBO).
uBO is awesome, made by an awesome person, and the awesome people that contribute to it. It's generally well liked, has huge install base, does what it says it does, no bullshit. I recommend it to all friends and family.
That said, personal and enterprise use case considerations are different. First party native solution vs some third party random (awesome!) dude on the internet.
This kind of goes to the point in the NSA advise, PDF linked towards the top. Might be great now, but what happens if it's compromised?
A first party native solution would be better, but it's still a net positive security and end user experience for most orgs.
We can mitigate a bunch of that risk, not all of it. If it goes bad one day, it's a race between you to administratively remove it, and the browser and OS vendors to nuke it. There in lies the trade-off, seems an easy one to me.
At time of writing, uBO relies on manifest v2, v3 basically blocks it. v2 is scheduled to stop working January 2023. Might all stop working / need some tweaks by then.
- https://developer.chrome.com/blog/mv2-transition/
- https://www.eff.org/deeplinks/2021/12/googles-manifest-v3-still-hurts-privacy-security-innovation
- https://www.theregister.com/2022/09/08/ad_blockers_chrome_manifest_v3/
- https://github.com/gorhill/uBlock
- https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/
https://chrome.google.com/webstore/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=en
install and configure⚓
Grab the policy templates.
https://dl.google.com/dl/edgedl/chrome/policy/policy_templates.zip
https://support.google.com/chrome/a/answer/187202
We'll need the GUID from the URL.
https://chrome.google.com/webstore/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm
Now here we define a policy in JSON that;
- force installs the extension
- prevents the extension from running where you don't want it to (based on URL patterns)
Suggest including addresses for the things you care most about the confidentiality and integrity of. General public web browsing, fine. Any admin interface to something important (PII is important), not so fine.
(really should only access those administrative things from a PAW, not the same browser / computer for everyday use. But happens more often than not.)
Also talk to HR, Finance, Payroll, Recruitment, etc; they'll have some addresses to exclude.
Baisc policy, modify to taste.
https://www.chromium.org/administrators/policy-list-3/extension-settings-full/
// TODO: write that browser hardening thing; block extensions by default, allow by exception
{
"cjpalhdlnbpafiamejdnhcphjbkeiagm": {
"installation_mode": "force_installed",
"update_url": "https://clients2.google.com/service/update2/crx",
"runtime_blocked_hosts": [
"*://*.azure.com",
"*://*.microsoft.com",
"*://*.microsoftonline.com",
"*://*.dash.cloudflare.com",
"*://*.console.aws.amazon.com"
]
}
}
Need to flatten / minify for the GPO part.
PowerShell, VS Code, CyberChef, jq; take your pick
Read-Host -Prompt 'it puts the json in the basket' |
ConvertFrom-Json |
ConvertTo-Json -Compress |
Set-Clipboard
GPO
User or Computer
Administrative Templates > Google > Google Chrome > Extension > Extension management settings
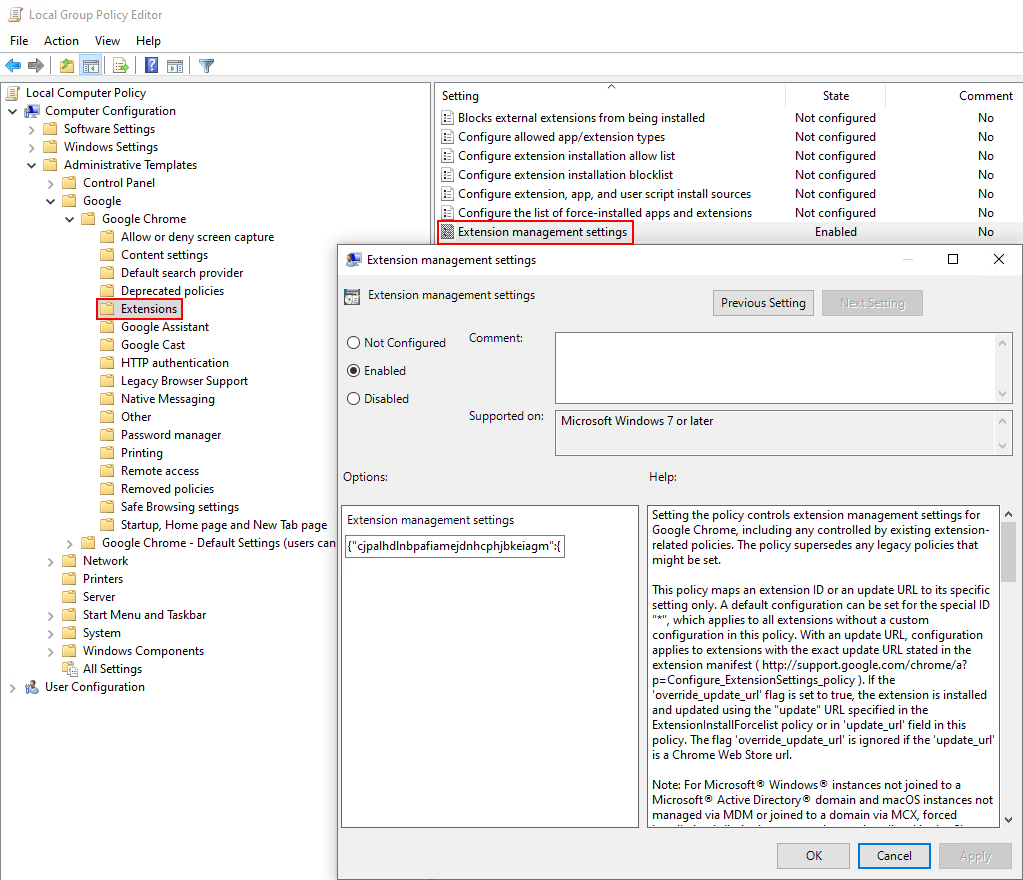
configure the actual extension⚓
We can also define some settings within the extension. By default uBO will add a context menu and an icon in the tool bar that has a counter for number of objects it's blocked on the page. Just more clutter and slight distraction, can turn it off.
showIconBadge isn't named great, the icon will still show, but i'll be nice boring static non-distracting icon.
https://www.chromium.org/administrators/configuring-policy-for-extensions/
{
"userSettings": {
"contextMenuEnabled": false,
"showIconBadge": false
}
}
Minify, push to registry (no admin template, that might come one day, no reason it couldn't be done with JSON).
Computer or user context.
// TODO: no syntax support for registry, log a feature request with Zola
// Using a weird syntax here to keep the line width down, easier to read on a phone.
HKEY_LOCAL_MACHINE or HKEY_CURRENT_USER
\SOFTWARE
\Policies
\Google
\Chrome
\3rdparty
\extensions
\cjpalhdlnbpafiamejdnhcphjbkeiagm
\policy
string
"adminSettings"
"{\"userSettings\":{\"contextMenuEnabled\":false,\"showIconBadge\":false}}"
test⚓
Open Chrome, go to chrome://policy/, Check the "status" column, should say "OK".
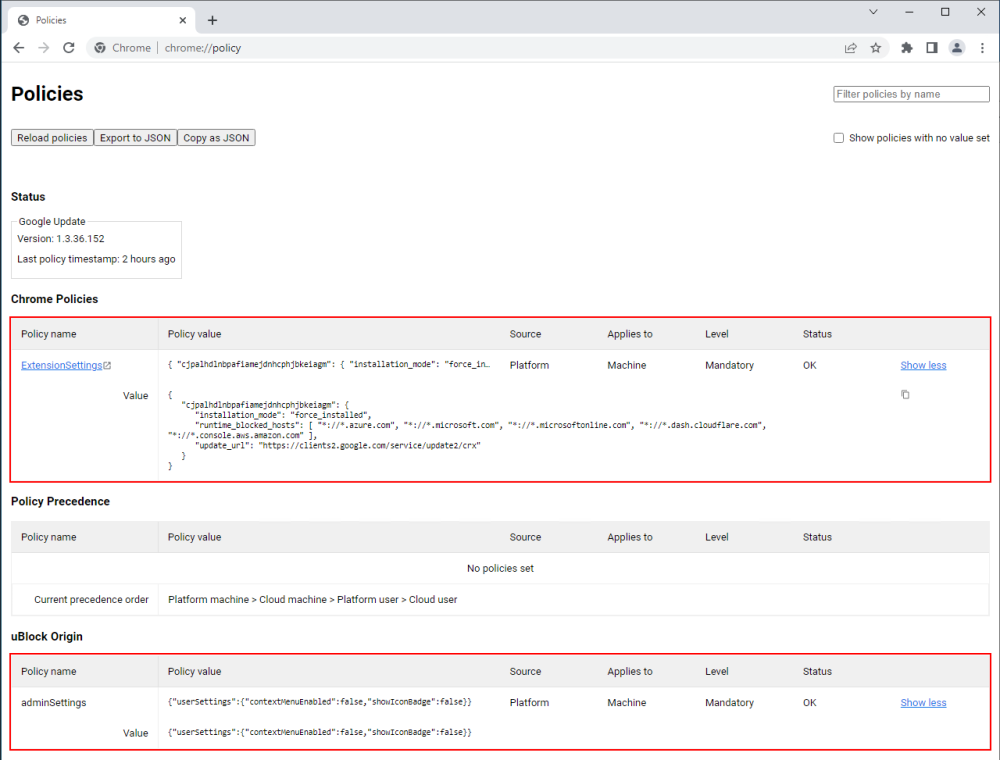
Find a web page with a bunch of ads, should now see less than normal. Should see an uBO icon in the toolbar.
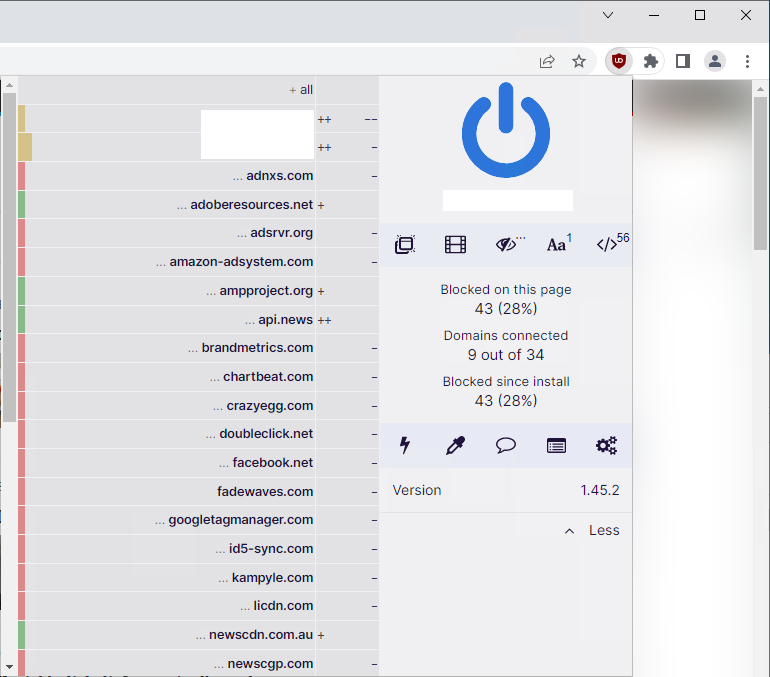
If you go to one of the excluded web pages from the above "runtime_blocked_hosts", at first glance it might look like the extension is there and working as normal. A side by side makes it a little more clear, still too subtle for my liking.
all done⚓
End users should be happy, less ads.
Network people should be happy, less contention.
SOC people should be happy, less alerts.
Everyone should be happy, excluding the ad people.